A mass filtration of 500 GB of data in the form of more than 100,000 documents has exposed a disturbing initiative. A startup called Geedge Networks is selling to governments around the world censorship systems modeled from “China Great Firewall“. There are at least three countries that are already applying restrictive measures similar to those of the Chinese government.
What happened. The leaked documents By interseclab They reveal how one of the investors in Geedge Networks is Fang Binxing, one of the “Parents” of the “Great Cortaygos of China”. Researchers have discovered that the startup markets an advanced surveillance platform that includes hardware for data centers and Software for local officials.
Intercepting everything. The central component of that platform is the so -called “Tiangou Secure Gateway” (TSG), a tool that acts as a gateway and that is installed in the data centers to process the Internet traffic of an entire country. All these data scan when this component is passed, and from there it is filtered and can be blocked so that it does not reach its destination. If the traffic is not encrypted, you can intercept and collect passwords and email addresses. If it is, it makes use of deep inspection systems of packages and automatic learning to detect and block tools that avoid these censorship systems, especially VPN.
Three countries already have their own “Great Firewall”. A consortium formed by media and human rights organizations (such as Amnesty International) identified that this platform is active in Kazakhstan, Pakistan, Ethiopia and Myanmar. In Geedge Networks they have published job offers for engineers willing to travel to countries such as Malaysia, Bahrain, Algeria and India, and are also hiring Spanish and French translators, which makes it clear that the startup is developing an important expansion strategy.
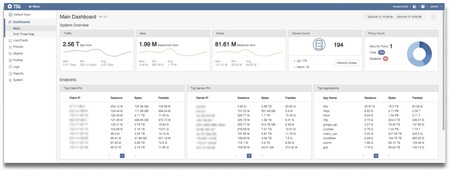

TSG control panel capture for Myanmar showing real -time traffic categorized in total bandwidth and active connections. Source: Interseclab.
An example of control: Myanmar. In a filtered capture the TSG control panel for Myanmar And it looks how the system was monitoring 81.6 million Internet connections simultaneously. In February 2024, Geedge hardware equipment had been installed in 26 data centers and 13 ISPS of Myanmar. There, 281 popular VPN tools were identified and the blockade of 54 of them was prioritized, including Expressvpn or Signal.
Growing suspicions. Although researchers warn that documents are not a definitive proof that this system is causing specific blockages, Geeedge’s records show strong correlations with certain important events of the past. In Ethiopia for example the TSG system changed passive monitoring mode to “active detention” of traffic just a few days before a remarkable internet blackout that It occurred in February 2023. There are other cases in which connectivity problems in these countries have coincided with events registered in TSG in filtered documents.
And incidentally, new Digitgal repression techniques in China. Among the leaked documents are also spoken of an active project in the Xingiang region, in China. There the startup has collaborated with Chinese research institutions to test a distributed firewall model instead of using a centralized one. There are also alarming experimental functions such as the ability to create relationships between users, group individuals according to applications that use or triangular the location of users through mobile base stations.
And the dreaded punctuation systems. There is also a prototype in which a kind of Score for the reputation of each userand that would apply individually. Each user would have a base score and to increase it would have to add personal data such as their national identification, data that allow facial recognition or employment details. If this score does not exceed a certain limit – or decreased due to the use of a VPN detected and prohibited, for example – the Internet access would be denied to the citizen.
Government malware. Another of the threats posed by this system is Geedge’s ability to Inject malware In user traffic. An operator could identify which website visit a user and, if it does not use a safe protocol (HTTPS), could inject malware directly into that connection. The researchers explain that although these experimental options are being tested in China, once the technology is mature, any foreign client can request those same functions on their platform to update it and have it available.
Image | Ran Liwen


GIPHY App Key not set. Please check settings