Few devices are as stable and discreet as the router. We barely think about them, we rarely review their configuration, and we rarely consider them part of the security debate. They are just there, connecting. This condition makes them ideal terrain for those seeking to go unnoticed. A recent investigation has revealed that ASUS routers are being used as part of a remote operating structure. They don’t cause problems, but they are no longer just an internet access point.
According to SecurityScorecardthe signal reveals the existence of something more than a specific failure. The researchers observed that a significant volume of ASUS routers exhibited the same TLS certificatewith a validity of one hundred years, which does not fall within the usual parameters of this type of equipment. This coincidence made it possible to identify a structured campaign, called WrtHug, and conclude that the devices had been altered in a coordinated manner to remain connected and operational without alerting their owners.
How WrtHug works. According to the analysis, the campaign is based on vulnerabilities present in ASUS routers and in the service AICloudwhich allows remote access to files and connected devices from outside the home network. By leveraging that channel, attackers can execute system-level commands and modify settings without requiring user intervention. The presence of the shared TLS certificate acts as a sign of this alteration and shows how the routers become part of an intermediary infrastructure, useful to hide the real origin of the activity.
AiCloud is a function integrated into ASUS routers that allows you to access files stored on USB drives connected to the router or in shared folders on a computer from outside the home. It can be used from a browser or through a mobile application, making it easy to view documents, photos or videos without being physically on the local network. That legitimate remote connection capability, intended for convenience, also means that any alteration to the system has broader consequences if an external actor comes to control it.
Which models are at risk. SecurityScorecard identifies several affected ASUS models, many of them old or end-of-life. Among those registered are:
- 4G-AC55U
- 4G-AC860U
- DSL-AC68U
- GT-AC5300
- GT-AX11000
- RT-AC1200HP
- RT-AC1300GPLUS
- RT-AC1300UHP
Some are still used in homes, but others are installed in small offices or businesses that have never renewed the equipment. It should be noted that although ASUS has published security patches and the vulnerabilities are officially corrected, research indicates that the majority of compromised devices are EoL (end of life) or outdated models. This combination of lack of support and obsolete equipment multiplies the risk that the problem persists over time.
Where the operation has been detected. The researchers observed that the compromised routers are concentrated in Asia-Pacific, with an especially high presence in Taiwan and other countries in the region such as South Korea, Japan and Hong Kong. Active devices were also registered in Russia, the United States and several Central European countries.
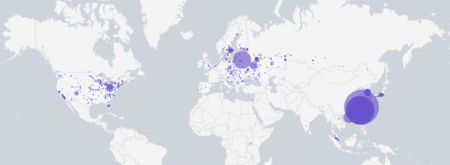

A map with the concentration of infected devices | Image:
A notable element of the report is that no cases were identified in mainland China, which analysts interpret as a contextual clue, although not proof of authorship. The geographical scope confirms that this is not a local phenomenon, but rather a distributed infrastructure.
What researchers say about China. SecurityScorecard does not definitively attribute the campaign, but notes that the behavior observed on the routers coincides with tactics previously used by actors associated with China. Researchers speak of “low-moderate confidence” that WrtHug is an ORB facilitation campaign operated by a pro-China actor, that is, a network of compromised devices that act as intermediate nodes to conceal the real origin of future operations. Among the technical parallels, analysts highlight similarities with a campaign called AyySSHush and the use of vulnerability CVE-2023-39780.

What to do if I have an ASUS router. Detecting if a device is compromised is not easy, because the changes introduced by WrtHug do not affect its operation. The first thing is to check if the model is among those that have stopped receiving support and install, if it exists, the latest version of firmware available from the ASUS website, following the recommendations of its security notices. As additional measures, it is advisable to disable remote services that are not used, such as AiCloud, review possible unauthorized access and consider replacing the equipment if it is already at the end of its life.
WrtHug shows that home routers are no longer a neutral element. They are devices always on, connected and with sufficient capacity to sustain discrete operations without altering their operation. This combination makes them useful pieces within a digital dashboard that previously seemed reserved for more complex systems.
Images | ASUS | SecurityScorecard


GIPHY App Key not set. Please check settings