Tokyo Tsushin Kogyo is one of the most solera companies in the technological world. He was born just after Second World War and his early years spent repairing radios and inventing appliances as a failed electric rice. As his name was so complicated for the West, they decided change it for something much simpler: Sony. Now surely the movie begins to sound because we are not going to discover the Importance of Sony and its innovation At this point.
But that innovation is not always positive and just 20 years ago, Sony committed the one that could be the biggest error in its history: install malware in the music CD they sold.
Oh, the MP3 … Although it was at the end of the 90s and the beginning of the 2000 when the MP3 format broke out in popularity, its story had already a few years behind it. It was in the 80s when a German engineer named Karlheinz Brandenburg developed a method to compress digital audio files without loss of quality being noticeable to the human ear.
The most purists of Flac will say that E MP3 is the devil, but the Brandenburg team used an algorithm that eliminated the sound information that humans do not easily perceive, thus reducing a barbarity the weight of those files. This opened a world of possibilities in the consumer and distribution industry: the MP3 portable playershe opened his way to the distribution of digital music and for the streaming of it. He also opened, two by two, the gap for the copy of songs and their illegal download.
To attack. Sony Music was already a giant of the record industry in the early 2000s. Now it is very combative with AIand in his day the MP3 did not make them a hint of grace. In fact, they were very aggressive about it. They were actively developing protection methods for their music albums and, in August 2000, Steve Heckler, vice president of the United States declared as follows:
“The industry will take any necessary measure to protect and protect its sources of income. We will not lose that flow of money. Whatever happens, Sony will take aggressive measures to stop this and develop technology that transcends the individual user.” You may think so, hard words, but it is too aggressive. Attentive because Heckler continued to affirm that they were going to put a Firewall To Napster.
“We will block it in your cable company. We will block it in your telephone company. We will block it in your Internet company. We will put a Firewall on your PC. They are aggressive strategies because, simply, there is too much at stake.” And what if they fulfilled their word.
XCP. It may be something that sounds to you due to how close the Conflict between LaLiga and Cloudflarebut Sony’s matter really was much more … curious. Shortly after Heckler’s statements, Sony launched Natalie Imbruglia’s second album with Anticopia protection Without announcing that it carried anticopia protection, but this was a plan that was already underway and the company launched certain albums with strong protection in some markets. In addition, before merging with Sony, BMG also launched millions of albums with some protection system.


The player | Image: Mark Russinovich
In March 2004, Sony and BMG formed a 50%alliance, marking muscle in the music industry and seeing how this strategy against song piracy had many points in common. The two companies had been hard about it and had declared that they would do what they had to do to stop the illegal distribution. Thus, at some point, they hired the services of Firts 4 Internet.
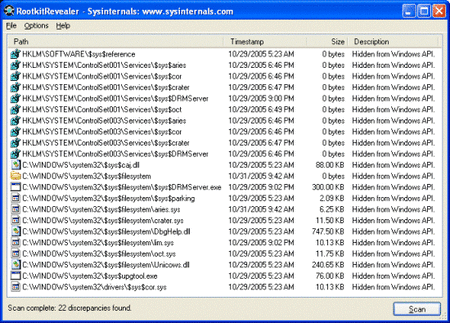
This company had a tool that seemed infallible: a system called Extended Copy Protection, or XCP. When a music CD was introduced with XCP on a PC, the self -arrange was activated and showed a license agreement that the user had to accept. If not, the CD was expelled and we could not reproduce it. By accepting it, we could enjoy the music and we would not notice anything … except for us to want to copy the files, since only three copies of the complete CD or three of each track were allowed.
Some points of that eula:
- If you got rid of the country, you had to erase all your music. If they stole the CD, too.
- By accepting, you assumed that Sony could install rear doors on the PC so that they can force compliance with their rights.
- In case of disagreement, the maximum sum for which you could sue Sony was 5 dollars.
Almost nothing, but the worst was not that.
It was … malware. But when the Eula was accepted, we were not only allowed to access the CD, but several programs were installed. They were the usual ones such as the protection itself, a Sony BMG player or the drivers to reproduce it. But there was something else, something much darker. So much that the users had no idea that accepting that agreement was infecting their PC.
The reason? Together with the other files, a rootkit called “$ Sys $ Aries” was installed that was automatically activated when starting the operating system and did everything possible to hide its processes. Even in the eyes of antivirus. This, as you can imagine, was a problem because hiding so deep in the system opened a huge security gap that could be used by malicious malware.


Mark Russinovich
Caught. They soon discover the cake. Mark RussinovichSoftware Engineer, unleashed the controversy when he published in October 2005 a blog post detailing the operation of this rootkit. Not only did he uncover the malware, but he indicated that the eula did not mention that software and denounced that digital rights management had gone too far.

Mark Russinovich
Russinovich was not anywhere: this Salamanca with American nationality is currently the Microsoft Azure Cto And XCP was not the only rootkit who brought to light (he did something very similar in 2006 with a Norton rootkit). The engineer, in addition to aiming at that creation of security holes, said he used insecure procedures to act, which could lead to system failures.
It was almost impossible to uninstall and, as it worked in the background, consumed PC resources, making it slower even when there was no Sony music CD in reproduction.
Answer. Sony had no way to deny his actions -although It was the first thing they did-, so they quickly launched software to eliminate rootkit, but the remedy was worse than the disease. Russinovich analyzed it and commented that what the new tool was doing was to unmask the hidden files that the rootkit had installed, but did not really remove the rootkit.
In addition, it installed a new software that could not be uninstall without a downloadable file to which you had access after giving an email address to Sony. And this was no longer a headache only for Sony and users, also for a Microsoft that had to get security patches. AND There were few albums …


Mark Russinovich
Consequences. In November of that year, Sony BMG launched a new tool that finally eliminated the rootkit, but the damage was already done. About 22 million CDs had been distributed with that protection method and Sony began to collect the unresses of the store. He faced complaints, allowed users to change their CDs with the anticopia method for new versions without the XCP and inspired security authorities to warn users not to install software from CD that they should not contain software, such as a music CD.
It was not enough and, in November 2005, Texas sued Sony BMG alleging that they were installing spy software in millions of CD and because “thousands of Texans are potential victims of this Sony deceptive game”, according to The State Prosecutor, Greg Abbott. Sony had no way out of that and was sentenced to pay $ 750,000 on legal costs, accept customer returns, put notices on their CD and pay up to $ 150 for each computer that had been damaged.
Other states, countries such as Italy or even the United States FTC added to the case, with their corresponding investigations and demands, and the company issued some Communities Informing whether in certain countries they had distributed CD with XCP, but as we said, the damage was already done and some cybercounts took note of the methods used by this rootkit to hide.
Apple so happy. Sony was the most aggressive, but not the only big record that DRM used in its CD, and this allowed Apple to hit a good bite to the portable players industry and the sale of digital music. While the largest records did not allow their users to create legal copies for their MP3 devices of the songs and albums they had bought, iTunes became the preferred platform to buy songs because who had a iPod I wanted to fill it … well, songs. AND They kept trying During 2007 with new DRM.
Thus, Emi, Vivendi, Warner in 2007 and, finally, Sony Bmg in 2008, announced that they got off the music ship with DRM to see if sales went back on their own OA platforms through others such as Amazon, hoping to give a bite to the apple of the iPod. The echoes of the Rootkit scandal continued to resonate and, in October of that same year, the alliance between Sony and BMG broke.
It was renamed again Sony Music And, despite that very serious stumble, it became the whale that is currently, being above others such as Universal and Warner Music.
Images | Mark Russinovich, Xataka
In Xataka | It seemed an impossible enemy, it was actually the brightest antipyretary system in a video game




GIPHY App Key not set. Please check settings