From names and ID numbers to names and bank account codes of more than 47 million taxpayers in Spain. That is, at least, the information that a cybercriminal claims to have obtained from the Ministry of Finance, and that he would be offering in at least one of the many forums dedicated to trading stolen data. The question is inevitable: are we facing a real leak? And, whatever happens, what should be done in a scenario like this? Let’s go in parts.
The alleged leak. As Hackmanac points outon January 31, a publication appeared in a forum frequented by cybercriminals in which a user called ‘HaciendaSec’ stated the following: “Today I am selling the updated Treasury database that contains the information of 47.3 million citizens.” In that same message, he detailed that the file supposedly included information associated with taxpayers such as:
- ID
- DNI/NIF
- Full name
- Address (type of street, address, address details, postal code, province, municipality, town)
- Telephone (country code, telephone)
- IBAN
- Last collected
- Total collection
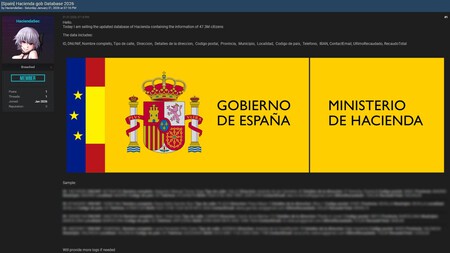

Capture of the forum with part of the information hidden for security
The usual goal: make money. It’s no secret: the main driver of cybercrime is usually money. And this case fits perfectly into that pattern. ‘HaciendaSec’ is offering these supposed data in exchange for financial compensation. We do not know the price of the database, but we do know the terrain in which these actors usually operate: payments in cryptocurrencies, a channel that allows them to receive illicit funds reducing, at least in theory, the possibilities of being tracked and identified.
The big question: has Treasury data been leaked? Here comes the key point. If we stick to the story of ‘HaciendaSec’ itself, it would be “an updated database.” The problem is obvious: to what extent is the word of a criminal reliable?
The user includes a supposed “sample” of the data, but this type of evidence says little on its own and does not confirm the real scope of the incident, or even if it exists as such. In these types of cases it is advisable to maintain skepticism: sometimes these are recent and legitimate leaks, but other times we are dealing with compilations of other breaches, data that has already been circulating for a long time, or outright hoaxes designed to sell smoke (and make money).
What the Treasury says. From Xataka we have contacted the Treasury to request comments on this matter. The official response, for now, is that they have no indication that their systems have been compromised. Of course: they also tell us that those responsible for security are working to rule out any type of intrusion. So, for now, we have to wait for more clarity about what happened. But in the meantime, it is advisable not to sit idly by.
What to do about the alleged ‘hacking’ of the Treasury. As things stand, we have two different levels: what the author of the publication claims and what the Treasury maintains, which maintains an internal investigation without conclusive signs of compromise. In such a scenario, the most sensible thing is to act prudently and take preventive measures. In short: be attentive, distrust by default and verify before accepting anything as good.
Anti-spoofing tools. We should be attentive to the campaigns phishing and impersonation, which is where many people end up falling. The Tax Agency remembers that it never requests confidential, economic or personal information, account numbers or card numbers from taxpayers by email, SMS or Bizum, nor does it attach annexes with invoice information or other types of data. Additionally, he recommends:
- Do not open messages from unknown or unsolicited users, delete them directly.
- Do not respond under any circumstances to these messages.
- Be careful when following links in emails even if they are from known contacts.
- Be careful when downloading email attachments, even from known contacts.
In Xataka | How often should we change ALL our passwords according to three cybersecurity experts


GIPHY App Key not set. Please check settings